THIRD PARTY RISK MANAGEMENT
Sciens Technologies offers comprehensive Third Party Risk Management (TPRM) solutions to help organizations effectively assess and manage risks associated with their business partners, suppliers, vendors, and other third-party relationships. Their TPRM services are designed to enhance security, mitigate operational risks, and ensure regulatory compliance.
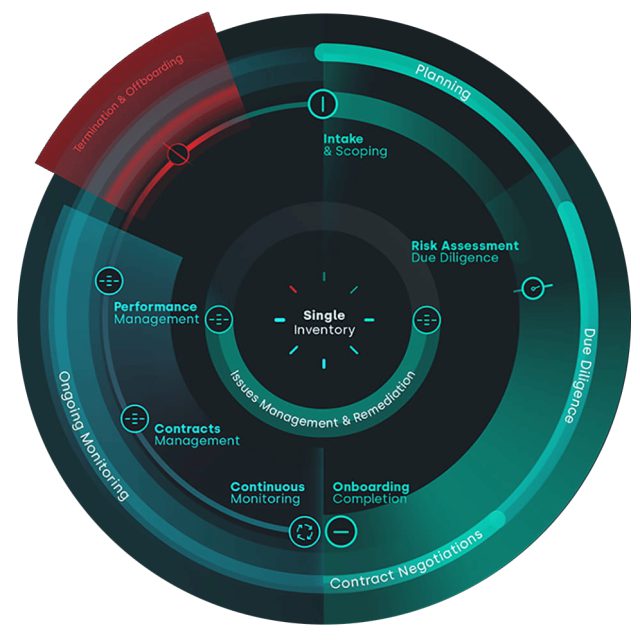

Here are some key components of the TPRM services provided by Sciens Technologies
Third Party Assessment: Sciens Technologies conducts thorough assessments of third-party vendors to evaluate their security posture, regulatory compliance, and overall risk profile. This includes evaluating their information security controls, data protection practices, business continuity plans, and adherence to industry standards.
Risk Identification and Analysis: Sciens Technologies helps organizations identify potential risks associated with their third-party relationships. They analyze various risk factors, such as the nature of the service provided, data access and handling, geographic location, financial stability, and any regulatory or legal implications.
Risk Mitigation Strategies: Based on the identified risks, Sciens Technologies develops customized risk mitigation strategies to minimize the potential impact of third-party risks. They assist organizations in implementing appropriate risk controls, security measures, and contractual agreements to address vulnerabilities and protect sensitive information.
Due Diligence and Vendor Selection: Sciens Technologies assists organizations in conducting due diligence on prospective vendors before entering into any business relationships. This includes evaluating the vendor’s reputation, financial stability, legal history, and security practices to ensure they meet the organization’s requirements and align with their risk appetite.
Ongoing Monitoring and Reporting: Sciens Technologies provides continuous monitoring of third-party vendors to ensure their ongoing compliance with security standards, regulatory requirements, and contractual obligations. They employ automated tools and techniques to track vendor performance, conduct periodic assessments, and generate comprehensive reports for organizational stakeholders.
Incident Response and Remediation: In the event of a security incident or breach involving a third-party vendor, Sciens Technologies helps organizations with incident response planning and execution. They provide guidance on containment, mitigation, and recovery strategies to minimize the impact of the incident and prevent future occurrences.
Regulatory Compliance: Sciens Technologies keeps up-to-date with evolving regulations and industry best practices related to third-party risk management. They assist organizations in aligning their TPRM processes with relevant regulations such as GDPR, HIPAA, PCI DSS, and other regional data protection laws.
Training and Awareness: Sciens Technologies offers training programs and awareness campaigns to educate employees and stakeholders about the importance of third-party risk management. They provide guidance on identifying red flags, conducting vendor assessments, and understanding the potential risks associated with third-party relationships.
Why is Third-Party Risk Management Important?
Disruptive events, have impacted almost every business and their third parties – no matter the size, location, or industry. In addition, data breaches or cyber security incidents are common.
- Internal outages and lapses in operational capabilities
- External outages affecting areas across the supply chain
- Vendor outages that open your organization to supply chain vulnerabilities
- Operational shifts that affect data gathering, storage, and security
TRPM- The Macro Picture
Across the board, third-party risk management is growing in importance, with many companies around the world in the process of developing departments to improve it. It is increasingly being viewed as an important investment companies must make to protect themselves from financial, regulatory, and reputational risk. This prioritization of TPRM is aligned with a push for centralization of processes and the standardization of procurement approaches, reporting, and risk management across companies.


Five steps to Third-Party Risk Management
No matter how you decide to address TPRM, there are five essential steps that will go a long way in minimizing risk.
- Identify – The first step is determining which companies you do business with that could bring about any type of risk. An understanding of this third-party ecosystem is critical.
- Classify – Taking a risk-based approach, you’ll need to identify how much risk each third-party places on your organization based upon data, system access, and service provided.
- Assess – Next, the security posture of the third parties you do business with must be evaluated. Depending on the nature of your organization, you’ll have varying levels of assurance based upon third-party risk.
- Manage Risk – Here, you’ll outline steps to put policies in place and decide how remediation should be addressed. Basically, you’re asking whether to accept or avoid risks.
- Monitor – The last step involves the continuous monitoring of third parties to ensure they meet contractual obligations and sustain their security posture.
Five steps to Third-Party Risk Management
The key Risk Pillars which are assessed in a TRPM model are
- Finance Risk
- Cyber Security Risk
- Environment, Social Governance (ESG) Risk
- Operations Risk
- Business Integrity Risk
- Supply Disruption Risk
By implementing a robust TPRM program, organizations can better understand and manage the risks associated with their third-party relationships, protecting sensitive data, maintaining compliance, and safeguarding their reputation. TPRM helps ensure that third-party vendors meet the organization’s security requirements and adhere to industry best practices.





